WARNING if you use fgdump like I did, it extracts pwdump to %TEMP% at run time, which is detected by AV.
First of all, I was floored when this worked. Really AV? It’s that easy? Really?
So here is the break down, go get “Resource Hacker“… You’re almost done. Only 3 steps left. (1 of which is optional)
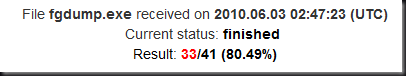
I started with fgdump, a well known hashdumping/pwdump tool. It’s detected by 80% of all AVs and by all the top 10. You see this on your AV report for your domain controller, and you’re having a bad day, probably week.
Watch this magic trick though:
[*] Step 1:
Open Res Hacker and drag a “normal” executable on to the window or Open File.
Click “Save All Resources”
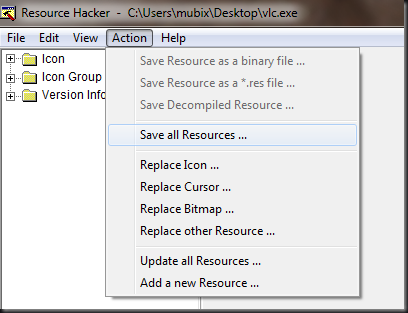
Essentially what you are doing in this step is simply extracting the .ico file (Icon) from the executable. Now you can do this with other tools, but we’ll be using resource hacker in a minute again, so it’s just easy to do it all with one tool.
We are done with this executable unless you are doing Step 2, in that case, leave it open, open another Res Hacker window and open your ‘evil’. (In our case, fgdump.exe)
[*] Step 2 (Optional):
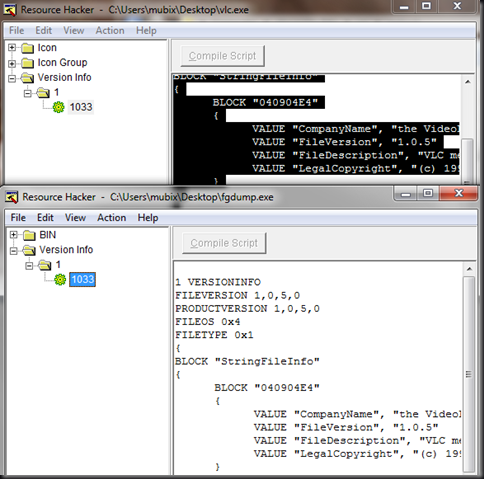
If you destination executable has tell-tale signs of it’s intent, much like fgdump as seen below:
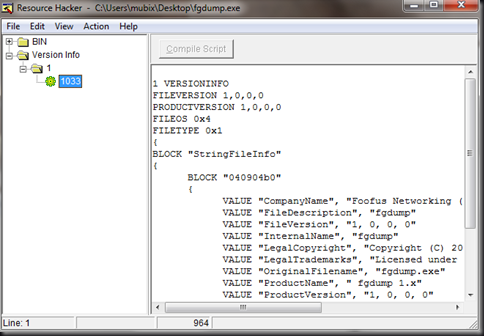
You can simply copy and paste the version info from your ‘normal’ executable into your new one and hit “Compile Script”:
[*] Step 3:
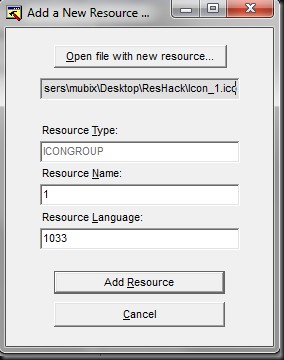
Next we need to “Add a new Resource” (our icon) into our “evil” binary.
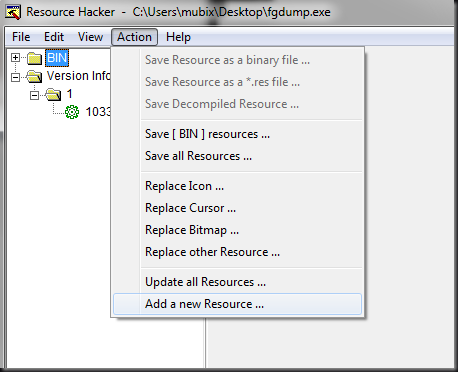
Once this prompt comes up, select the ICO file that shows the icon you want it to have (some binaries have a ton, so make sure it’s the right one). Put in ‘1’ for resource name, and ‘1033’ for your resource language. (You can play with these values, not sure what impact they have, but from the binaries I’ve looked at those values are pretty standard for a windows executable).
Save your new awesome binary as something else, I chose vlc2.exe
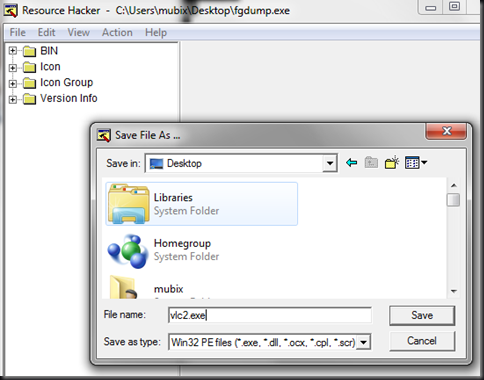
And… (drum roll)
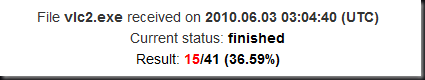
Tada! Sad isn’t it? Only 1 of the top 10 AV now detect this binary. Good job AVG and Avast! You still picked it up, but Trend, Symantec, Microsoft, ClamAV, Kaspersky, Panda, Norman, NOD32, Sunbelt, F-Secure, Fortinet, BitDefender WTF guys!?
Oh and Kaspersky now flags it as “not-a-virus” but still flags it.