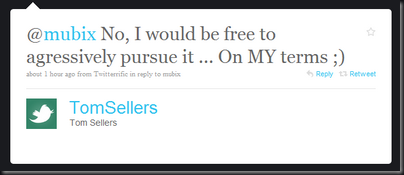
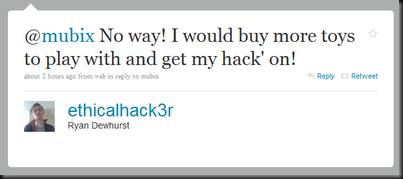
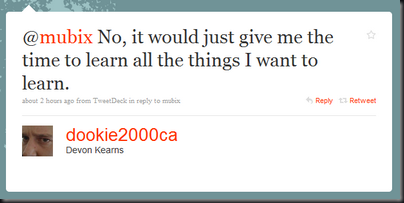
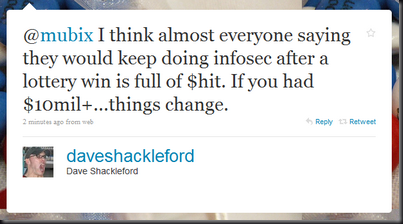
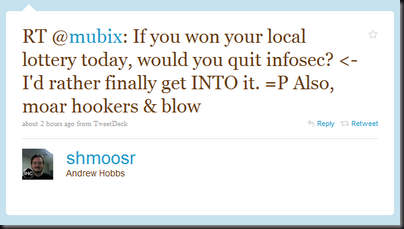
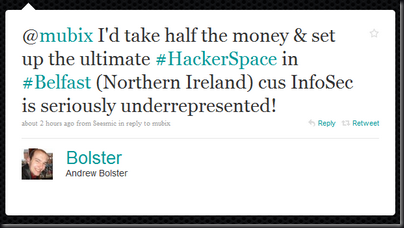
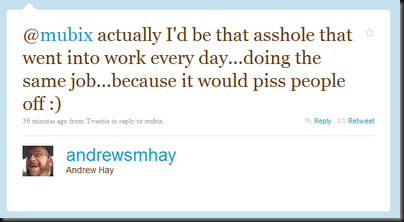
I have an admittedly limited view of the exploit dev world. However, from what I’ve seen devs have very few options: (Please correct me if I’m wrong)
Responsible Disclosure
- Direct Contact => depending on the size of the vendor and their view on security, this could result in anything from a simple thanks, a reward, to a court hearing.
- Exploit Broker => possibly sell, possibly not, depends on the broker. The vuln could die on the table or stolen due to too much information being given during negotiations. This route has the same financial risk as direct contact, but a lot less risk of getting sued.
- ZDI (or other vuln clearing house) => “instant” cash, but admittedly less than an Exploit Broker could possible get based on the financial risk to ZDI. Close to zero risk of court time (they may come after you for selling the exploit). And a lot less financial risk since (IIRC) they pay up front. But then the vulns go to also undisclosed parties, potentially the highest bidder which is probably not the vendor.
- “other” secretive groups who share vulns for different reasons…
- Just to friends => No cash, no judicial risk, but you do risk them stealing/selling your exploit.
Full Disclosure
- Posting it to the web for all to see/user => Possible court time, but the definite upside is the vendor is forced to react. A very quick way to make enemies.
- Releasing at a conference => Probable court time.
No Disclosure
- Keeping it to yourself => Working under the assumption that your the only one that has found that same bug is still semi relevant due to the incredibly small size of the exploit dev community. However, as Dave said, they’ll be toasting to their sleeping dead 0days some day.
No More Free Bugs
- My stance on this is split, while I think people should get paid for their work, I relate this movement to mowing someone’s lawn and then ringing their doorbell and asking for money. However I’m sure Robert Graham’s punch in the face metaphor also works.
Like, I have stated above, I am far and away a newbie to the vuln disclosure world and this debate has been going on since before I owned my own computer, but with the brilliant minds working at it, why doesn’t anyone offer up a solid solution to it?
My solution? Create a standard, something that we all abide by. I know as hackers we rebel against such things but in the interest of getting better security out there (yes, that’s what we are here for right?…. right?) we should should really work together on this. What sounds right?
I mean, what is the right way to approach someone who’s lawn you’ve mowed for the work you have done? Maybe free for open source projects, and a price based on exploitability and market share of the affected product?
Reference:
Vuln Trading Markets and You by Michal Zalewski (lcamtuf):
=> http://lcamtuf.blogspot.com/2010/04/vulnerability-trading-markets-and-you.html
Vuln Disclosure is Rude by Robert Graham:
=> http://erratasec.blogspot.com/2010/04/vuln-disclosure-is-rude.html
No More Free Bugs movement by Charlie Miller, Alex Sotirov and Dino Dai Zovi:
=> http://trailofbits.com/2009/03/22/no-more-free-bugs/
Dailydave Post by Dave Aitel:
=> http://lists.immunitysec.com/pipermail/dailydave/2010-April/006100.html