Keeping it here for notes and just in case anyone else runs into this same issue.
1 2 | |
If you have a better way please leave a comment below!
Keeping it here for notes and just in case anyone else runs into this same issue.
1 2 | |
If you have a better way please leave a comment below!
This is my box. There are many like it, but they are all mine.
My malware is my best friend. It is my life. I must master it as I must master my life.
My malware, without me, is useless. Without my malware, I am useless. I must drop my malware true. I must rootkit better than my enemy who is trying to kill my binary. I must kit him before he kits me. I will…
My malware and I know that what counts in this war is not the boxes we pop, the noise of our root dance, nor the cheers coming from the Red Team room. We know that it is the root that count. We will root…
My malware is human, even as I, because it is my life. Thus, I will learn it as a brother. I will learn its weaknesses, its strength, its parts, its extensions, its dlls and its exes. I will keep my malware av free and ready, even as I am ready. We will become part of each other. We will…
Before God, I swear this creed. My malware and I are the defenders of my botnet. We are the masters of our enemy. We are the saviors of my shells.
So be it, until victory is the Red Team’s and there is no enemy, but peace!
So there was this blog post that talking about a number of ways to dump windows credentials by @lanjelot [definitly someone to follow] – here: https://www.securusglobal.com/community/2013/12/20/dumping-windows-credentials/ and at the very bottom of this post it says “AD Replication (EXPERIMENTAL)”
What it boils down to is if you can position a system that can do DNS resolution to the target domain, and perform some other UDP traffic, you can fake join a samba server you control to a domain and it doesn’t require code execution in any way on the domain controller.
Notice: I am not doing this on a Kali Linux box, there is already an install of Samba there and I didn’t want to try uninstalling or modifying the one installed.
First, you need this patch:
wget http://files.securusglobal.com/samba-4.1.0_replication-only-patch.txt
and Samba 4.1.0
wget http://ftp.samba.org/pub/samba/stable/samba-4.1.0.tar.gz
You will probably also require some dependencies to be installed:
apt-get install python2.7-dev python-samba libacl1-dev build-essential libldap2-dev libkrb5-dev attr
Since the patch is kinda wonky, you need to make a src directory and extract samba into there first. Then apply the patch in whatever directory is above src
1 2 3 4 5 | |
So it would look like this:
1 2 3 | |
then run patch -p0 < samba-4.1.0_replication-only-patch.txt
1 2 3 4 | |
Prepare the box:
1
| |
Next you need to make sure you are resolving correctly (if you can’t resolve the SRV record _ldap._tcp.sittingduck.info (sittingduck.info being the domain) then this isn’t going to work.
1
| |
Then start the clone:
1
| |
Looks like this:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 | |
Then to get the hashes:
1 2 3 4 5 6 7 8 | |
Or you can do it with history:
1 2 3 4 5 6 7 8 9 | |
Game over. The great thing is that it never actually shows up as a joined box in the domain, and as far as I can tell the only log on the real DC is the login success of a domain admin. Plus one of the huge benefits to this method is that once you have the database Samba makes it really easy to query information like group membership or users info after the fact, not just hashes.
PSEXEC has been a staple for Windows post exploitation pivoting and system administration for a long while. The basic premise of how all “psexec” tools work is:
Now, as you can guess, the uploading of a file, creating, starting, stopping, and deletion of services create quite the logs and forensic evidence.
As you might imagine, thats not the best thing for us on the offensive side of infosec. Luckily big brother Microsoft provides another option, WMI (Windows Management Interface). I demonstrated the use of this in the past: HERE and HERE
The downside to using the WMIC directly is that you need a valid token or a valid password for it to work. Passing the hash didn’t used to be an available option.
That has changed with the “wmis” package on Kali Linux that incorporates the “Pass-the-Hash for 15 years toolkit”
(There is a slight problem where you have to play with it a bit to get it working on 64 bit Kali)
The other solution is supplied as an example in the Impacket library “wmiexec.py”. In my experience there are a few features that make it the better option.
Enough crazy talk here is an example usage of each:
1 2 3 4 5 6 7 8 9 10 11 | |
1 2 3 4 5 | |
Using a password, but with hashes you just tell it -hashes :
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | |
Everyone has their list of hostnames they brute force domains with. In my last post I even mentioned a few ways to use one with XARGS or PARALLEL. But one fact about wordlist brute forcing is that there is no “one list to rule them all”. But over the years of doing DNS record collection I have noticed one thing, most domains have a large number of short hostnames that are easy to remember, usually 4 characters or less.
I’m sure you already know where I’m going with this, I wanted to brute force all possible hostnames up to 4 characters. For a long time I struggled with coding this, but couldn’t wrap my head around it. I would come back to it every so often, finally a few days ago I happened upon a script on gist: https://gist.github.com/petehamilton/4755855 that suited my needs perfectly.
I modified it to suite my needs (just use the yield method) and here is what I ended up with (remember DNS is case insensitive):
Notice: This script doesn’t end, it will keep doing lookups on longer and longer hostnames until you hit CTRL-C
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 | |
This worked but it was slow, so I sped it up using methods that I talked about in my last post and a quick modification:
I used this:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | |
which just prints all the possibilities:
1 2 3 4 5 6 7 | |
and piped it into parallel + dig:
1
| |
and got the following:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | |
Happy bruting. Both scripts can be found on my gists page:
Quick update: As @MikeDamm points out, xargs has a -P option that can do the same thing I’m using parallel for. If you have a supported version of xargs you can use -P 0 to do the same thing as -j0 with parallel, but if your version doesn’t support the 0 you can simply use the same number parallel uses ala:
cat subdomains.txt | xargs -P 122 -I subdomain dig +noall subdomain.microsoft.com +answerThis results in roughly the same completion time as it’s parallel counterpart. Thanks @MikeDamm!
There are some great discussions on the NoVA Hackers mailing list. One such discussion was about what the best way to do dns hostname brute forcing was and which tool is better than another. For me, I just use the command line and then parse the results (or just ask the deepmagic.com database ;–)
Here is what I do:
First, you need a good list of DNS sub domains / hostnames. Personally I use the list provided over at http://www.ethicalhack3r.co.uk/zone-transfers-on-the-alexa-top-1-million/ (with a few minor tweaks). If you haven’t read that post and follow-on posts you really should. But take the list and save it locally. Then just run the following command:
cat subdomains.txt | xargs -t -I subdomain dig +noall subdomain.microsoft.com +answerNow, xargs is great but does one thing at a time and can be quite slow if your subdomains list is large. With the use of the amazing tool GNU parallel you can get done in a matter of seconds, well, that or knock over your home router.
cat subdomains.txt | parallel -k -j0 dig +noall {}.microsoft.com +answerWarning: the -j0 option maxes out the possible file handles and jobs that your CPU/kernel can handle, which usually destroys VMs. Just a smaller job count like 100 or 50 if you want the speed without the crash ;–)
with an output something list this:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 | |
There was a recent presentation at DerbyCon, entitled:
Living Off the Land: A Minimalist’s Guide to Windows Post-Exploitation by Christopher Campbell & Matthew Graeber
I highly recommend that you start with this presentation as it lays the foundation for this post.
The premise is, how can we maintain persistence in a corporate environment, using tools and defaults provided by the host OS we have compromised. This is a very important concept, given the shift in many organizations to an Application Whitelisting Defense model.
It is only a matter of time before time before you might encounter an Application Whitelisting Defense.
As a follow up to that presentation, I began exploring the binaries that ship by default with Windows. That is where I stumbled across a binary in the C:\Windows\Microsoft.NET\Framework64\v2.0.50727 path.
The Executable is ieexec.exe. A write up is here: http://support.microsoft.com/kb/822485
“The IEExec.exe application is an undocumented Microsoft .NET Framework application that is included with the .NET Framework. You can use the IEExec.exe application as a host to run other managed applications that you start by using a URL.”
Excellent! So, now we just need to host our malicious binary , and call it from ieexec.exe.
This is great, since most Application Whitelisting Environments are going to “Trust” anything signed my Microsoft as a matter of convenience. IEexec.exe will download and execute our code for us, all under the trusted process.
So lets get started!
Step 1. Prepare your Shellcode, or whatever malicious app you want. I compiled my executable using SharpDevelop, since it has less footprint than a full blown Visual Studio install. From msfconsole:
1 2 3 4 5 6 7 8 | |
Step 2. Create the .NET wrapper application
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 | |
You will want to compile the exe for the target platform. In this case I am going for an x64 target. Also, you will want to compile for 2.0 or 3.5 Framework.
Step 3. Host the Exe. For this example, I used Mongoose. Simple and Effective:
http://code.google.com/p/mongoose/
By default Mongoose listens on port 8080. This is configurable. Simple place your compiled binary from step 2 into the same directory as Mongoose. Start Mongoose and you are almost ready to deliver your payload.
Step 4. Setup your receiver:
1 2 3 4 5 | |
Step 5. From the host that is protected via Whitelisting. Open 2 Command Prompts as administrator.
CMD 1 Execute:
1
| |
 CMD 2 Execute:
1
| |
There is some detail to unpack here, I can go over later, as to why we need to run caspol.exe. Here’s the behavior I saw in our experimentation with this.
Initial attempt to run our rogue binary fails, since it is unknown/untrusted/unapproved:
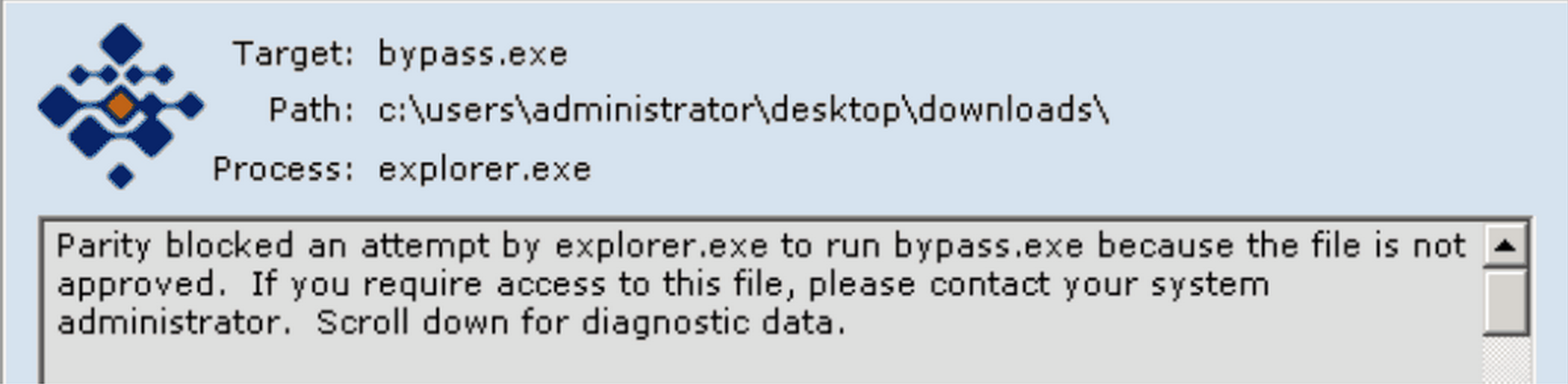
Now, on the same host…
Executes just fine!
Its important to distinguish what this technique is and what it is not. This is not an exploit or vulnerability. Rather this is one way to execute arbitraty code in an Application Whitelisting Environment.
Summary:
In this document we learned that even if a host is in a mode where only trusted approved applications can run. IEexec.exe can be used in certain situations to circumvent a Whitelist, since it is likely a trusted binary, since it is signed by Microsoft.
Cheers,
Since I’ve been gone, OJ has released the ExtAPI (Extended API) for Meterpreter. This has some pretty amazing functionality. You can find OJ’s write up on it and more amazing things he did in 3 months of meterpreter and on the Metasploit blog.
Just brushing the surface and to help people see the power of this new functionality I went ahead and created a few Meterpreter scripts that can really mess with someone.
1st is a script that loops through all of the windows for your current user and sets the focus to them in rotation. Essentially making their machine unusable.
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
2nd just sets all of the windows title’s the say “hacked”
1 2 3 4 5 6 | |
and finally if in Windows if you close all of the windows, including “invisible” ones like Explorer, you will essentially make the machine unusable.
1 2 3 4 | |
OJ suggested a few other options:
Destroy:
1 2 3 4 | |
or Minimize all:
1 2 3 4 | |
Thats it for now, next up we will do a few things with services as well as the clipboard. Stay tuned!