With the use of Mimikatz and WCE, clear text passwords are much more common. What isn’t always there is the user. They take lunches, go home at a reasonable time and generally aren’t really appreciative of our (pentester/red teamer)’s schedule.
A straight forward way, and provided by Microsoft to create a process as a user (whereby having their token readily available is using ‘runas.exe’:
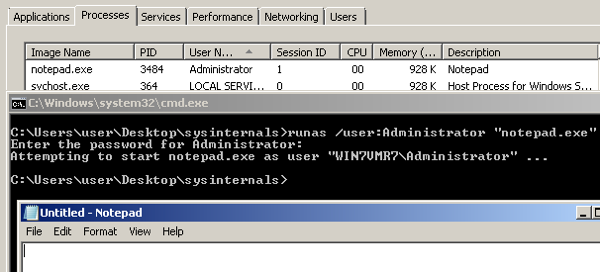
w00t, we the user is present, we can migrate our meterepreter session into that notepad and we’re good right? Problem there is you have to interactively input the password, so without a real cmd.exe or RDP session of your own, (VNC payload would work), you’re generally SOL.
There are a ton of posted ways around this, most involve make a wrapper script to input the password for you such as this one:
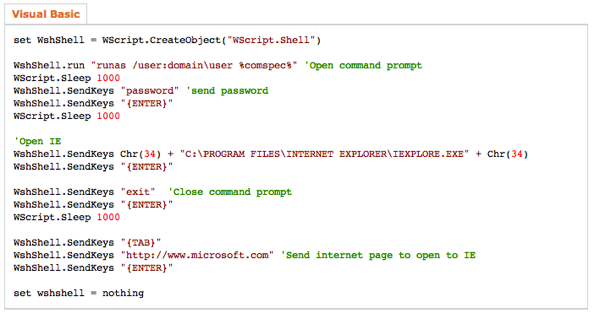
(this was pretty unique as it actually sent the keys to the key buffer instead of directly to STDIN)
Another way if you don’t mind dropping / creating a custom bin, AutoIT makes this REALLY simple:
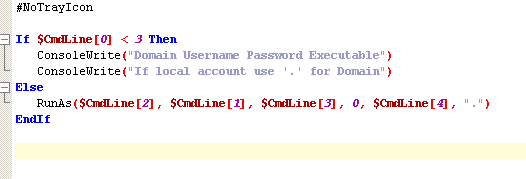
This could be 2 lines if you really wanted it to be but I like to make things a bit more universal. You could also execute this directly in memory with meterepreter’s execute command with the “-m” argument after you’ve built the AutoIT script into a EXE.
But what go through all that trouble? Railgun can do this just as easily. Drop to IRB or create a script that does the following:
1 2 | |
This will create a notepad.exe process with the defined user. But we can go a bit more stealthy, since we really only need their account token we can just user LogonUser:
1
| |
List the tokens available with Incognito, your new user will be there, steal it and you’re done. You now have the ability to user that account/domain token on any of the hosts you’ve compromised on the network, not just the ones they happen to have left themselves logged in. This gets really fun on servers where the admin hasn’t logged in but you wanna grab all of their IE saved passwords ;–)