Idea came thanks to cktricky from: http://cktricky.blogspot.com/
A bunch of sites on the web give you different pages depending on the browser you use to view it. I know when I was a web developer compatibility was the bane of my existence, as I’m sure it still is for all the web devs out there. Well, sometimes this leads to bad coding practices, or even the old “Google Bot gets to see everything” feature. Well, I had an idea to take Burp’s Intruder and “Brute Force” any compatibility coding that a site may have. Especially if there is a restricted section of the page that you know is there, but don’t have access to.
To start off you need a list of user agents. I pulled mine from the User-Agent Switcher lists I found on the web since they are in easily parsed XML.
From: Qainsight’s UA Lists.
I downloaded: http://qainsight.net/content/binary/AgentStrings20070517.xml
There are plenty of ways to parse XML in your scripting language of choice but here is some dirty bash script that worked for me:
1
| |
Next, we set up our Intruder instance:
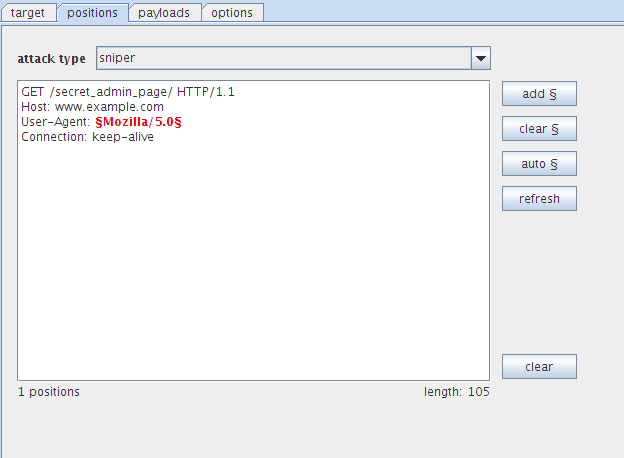
And import useragents.txt into Intruder and kick it off.
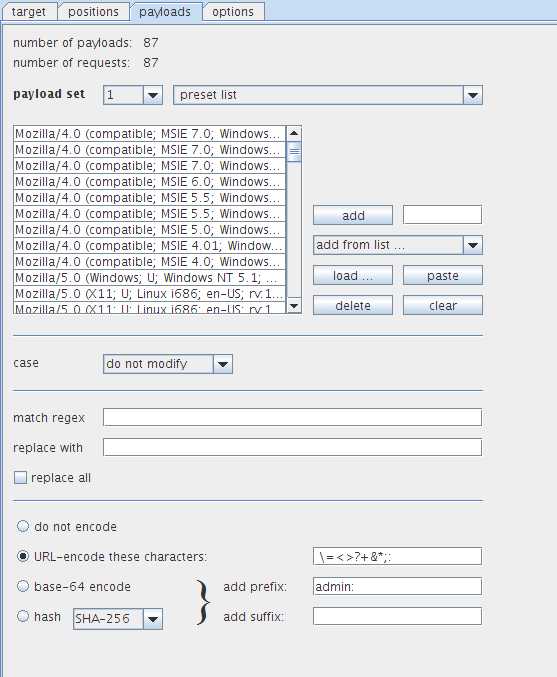
If any of the ‘payloads’ come back with anything different, it’s definitely something to look into.