pfSense is an excellent free way of including a firewall / ids / proxy in your lab or VMs. It runs small and fast, but even as simple as pfsense is sometimes you need a bit less complexity and speed of configuration.
Enter Peerblock and AnalogX’s proxy. Two free tools, one usually used to stop people who torrent from getting caught by the RIAA/MPAA and the other a drop dead simple windows based proxy utility.
First we’ll talk about AnalogX’s proxy, you can get it here:
http://www.analogx.com/contents/download/Network/proxy/Freeware.htm
A simple next->next->finish install gets you this:
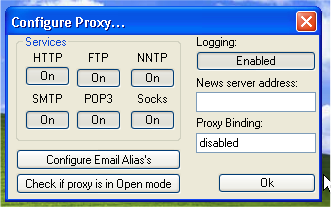
With the following ports listening:
- HTTP (web browsers) (port 6588)
- HTTPS (secure web browsers) (port 6588)
- SOCKS4 (TCP proxying) (port 1080)
- SOCKS4a (TCP proxying w/ DNS lookups) (port 1080)
- SOCKS5 (only partial support, no UDP) (port 1080)
- NNTP (usenet newsgroups) (port 119)
- POP3 (receiving email) (port 110)
- SMTP (sending email) (port 25)
- FTP (file transfers) (port 21)
So you can test everything to your hearts content that it goes through a proxy, using any proxy type you want basically.
(I will assume here that you know how to setup your own proxy settings for your OS)
But the problem being that if your code / application misbehaves it will still get out. You could go to the trouble of fiddling with the Windows firewall if you are running Windows 7 (not sure if XP can box egress, probably can). But I like simple and straight forward solutions.
PeerBlock can be found here: http://www.peerblock.com
And is simple to set up as well (next->next->finish applies).
Go into List Manager once you have it installed and “Create a List”
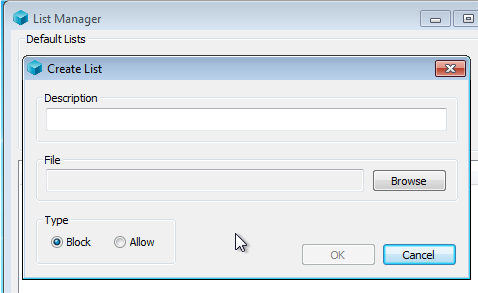
Give it a description and a place to save the file:
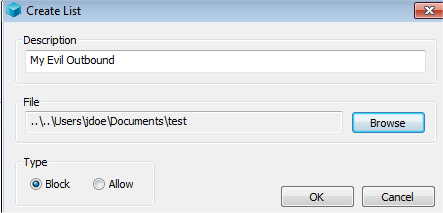
You’ll get this window automatically pop up, but if you don’t you just click ‘Add’ with your custom list selected in the List Manager:
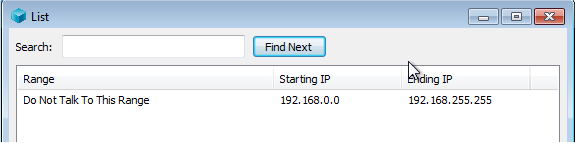
Feel free to block everything but one IP, a range, or whatever your meets your needs, nothing in or out from or to that IP/Range will be allowed
One of the uses I use it for is blocking the whole Internet except for my internal ranges for stuff like my personal Virus Total lab where I run bins to test stuff out, that way the AntiVirus services can’t ship my bin off to who knows where to be analyzed before I even get to use it.
Here is an example of my “All the Internet” block list:
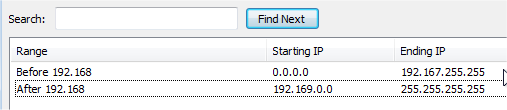
Thats everything for now, hope some of it was useful in your setup and experiments ;–)