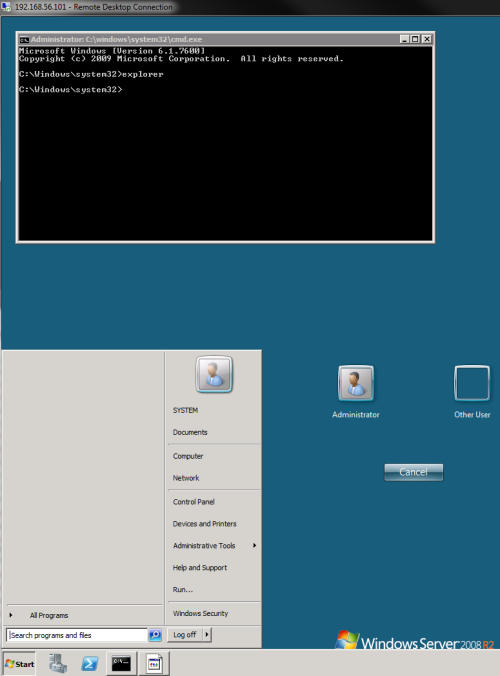
At CCDC, Sticky Keys via RDP was a very successful re-entry point for the Red Team. You can read more about how this works here:
http://carnal0wnage.attackresearch.com/2012/04/privilege-escalation-via-sticky-keys.html
So if you can get physical access or SYSTEM/Admin access at some point and enable + reach RDP, you can very easily follow those instructions and gain a level of persistance without the need of a pesky password :–)
However, this doesn’t work so well with the advent of NLA or Network-Level-Authentication, which was enabled for Vista systems and beyond. In particular Win 2008 R2 uses it by default. StickyKeys don’t work so well if you have to authenticate first. Boo!
But, if you are already on a box with Admin access for a time, you can make one additional change so that you are back to Sticky Key and Utilman heaven.
HKEY_LOCAL_MACHINESystemCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp
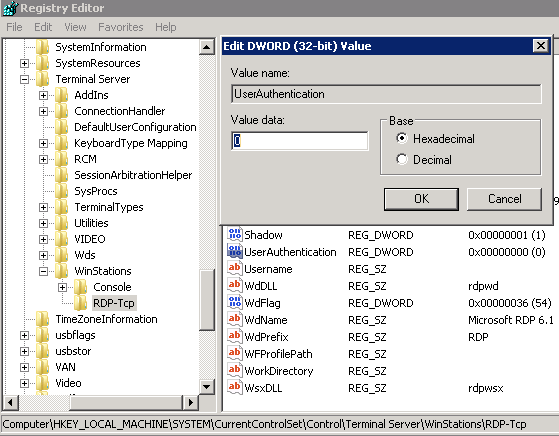
Change the value of UserAuthentication value to 0, and instantly you are back to slamming the shift key and popping system shellz.
— mubix
P.S. I ran into permissions errors when trying to copy cmd.exe over sethc.exe and utilman.exe:
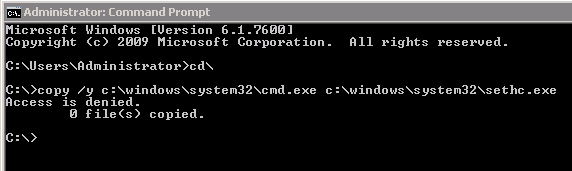
But a brilliant fix to this annoying security control ;–) was provided here:
By setting CMD as the debugger for sethc.exe or utilman.exe Windows executes the debugger first, so back shelling again.