In Revision 7315 of the Metasploit Framework (SVN) a new option was added to MSFENCODE. Technically you always had the ability to do the following, but it required a bit of knowledge of the inner workings of the framework.
But before I get into the new feature, lets quickly go over the standard way you use msfencode:
1 2 3 4 | |
We just used MSFPAYLOAD to output in [R]AW format, a reverse tcp connect meterpreter payload. We then piped it into MSFENCODE, so that we could output it as a proper Windows executable (/tmp/bob.exe), encoded to avoid AV detection.
Now if you knew where it was (data/templates/template.exe) you could probably just replace the template.exe with the one you want loaded with the payload and called it a day. But then you wouldn’t get some of the tweaks that make this update awesome.
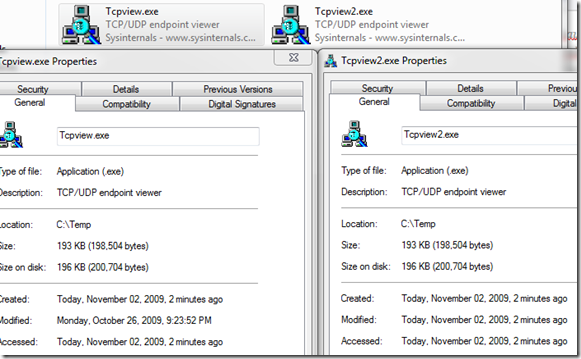
The update added the (-x) option to msfencode. This allows you to specify an executable of your choosing to sacrifice to the gods. For example: (TCPView)
1 2 3 4 5 | |
And if everything went well, we have a nice new executable in /tmp/ called Tcpview2.exe. Want to know the magic part? Try to tell them apart: